On 3 June, James Jackson, S-RM’s Senior Associate in Cyber Security and member of the S-RM Cyber Incident Response team, published a detailed and original investigation into the ransomware and associated cyber threat group known as RobbinHood.
We interviewed James to find out more about what motivated his research, what he uncovered and how it can contribute to both S-RM’s and the information security community’s efforts to tackle ransomware attacks in the future.
Q: What is RobbinHood?
JJ: RobbinHood is a type of ransomware, a malicious application that will encrypt files on your computer and demand a ransom to decrypt them. But it’s also a threat group, that is, the people that operate it identify with the ‘RobbinHood’ moniker. They were first spotted in April and May 2019, with ransomware attacks targeting the US cities of Greenville and Baltimore, but have kept a relatively low profile since then.
Q: What piqued your interest in them?
JJ: During incident response engagements at S-RM, we routinely come across different threat groups and malware samples. Most of them are very similar and operate in the same ways. In a recent response case, we encountered RobbinHood. And while they exhibited much of the traits of other ransomware groups, the way they have developed and automated their attack is something I found really interesting. Not necessarily because they are doing anything new or particularly advanced, but because it demonstrates how the threat group have reacted and adjusted their operating model to increase the effectiveness of their ‘business’ over time – looking into them offered a rare glimpse into how the people behind ransomware think.
Q: What were your main findings?
JJ: My research, combined with learnings from direct involvement with the group through recent incident response work, has shed some light both on how the ransomware works, as well as who RobbinHood might actually be and how they operate.

The Ransomware
For starters, I described the functionality of the latest version of the ransomware and how it encrypts files. Having this information on hand will provide an immediate benefit to anyone dealing with this ransomware group and who needs to understand what it did to their computers.
But, beyond that, I also analysed the attack method this threat group uses to spread their ransomware inside a victim’s network and identified several tools that they had developed to accomplish this. These tools work together to get rid of the defensive software that might be present in their victim’s environment. The infographic below summarises my findings in this regard:
RobbinHood’s Toolkit:

Attack Reconstruction:
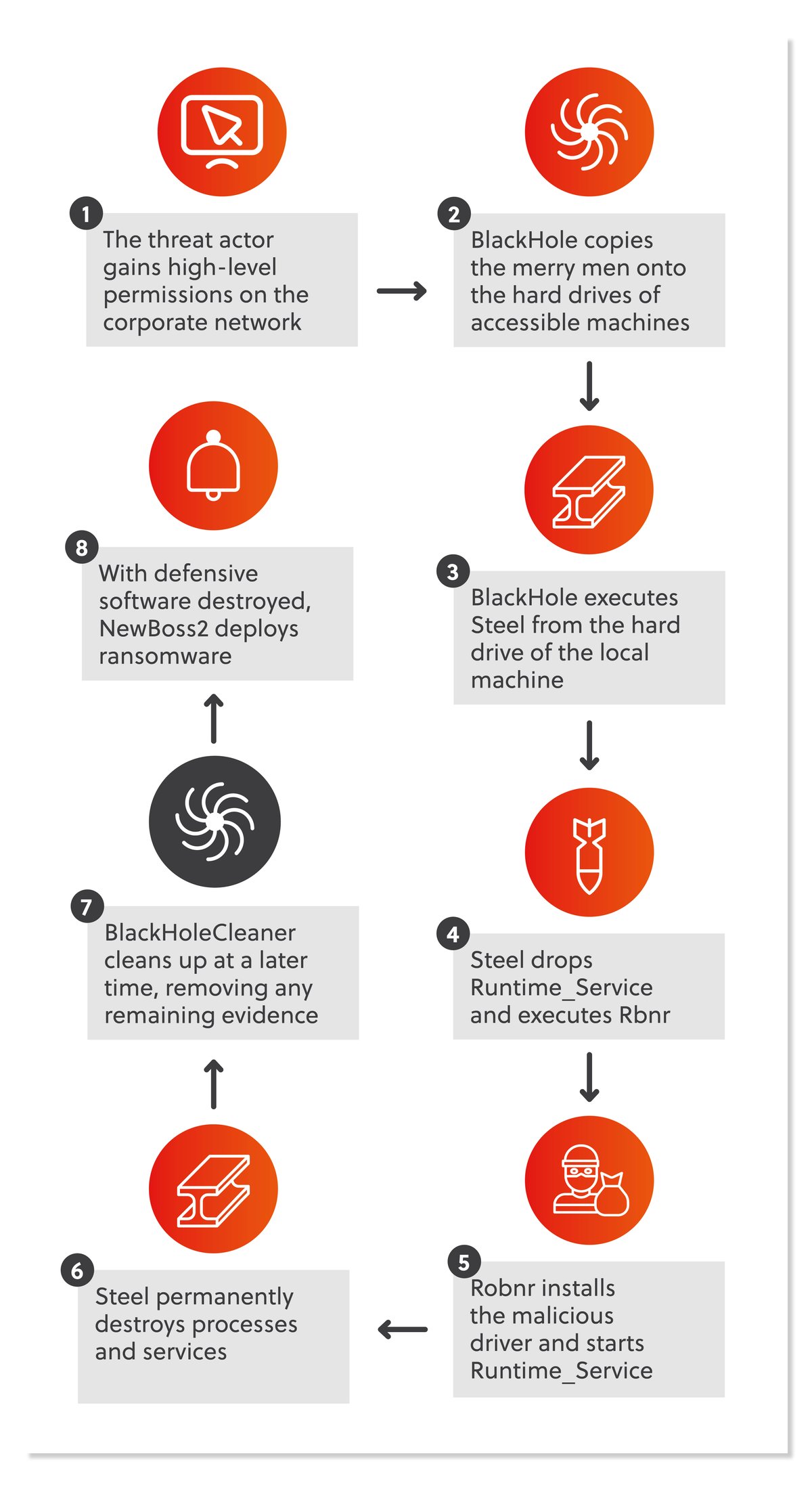
Understanding the attack method in this detail will allow other incident responders and security analysts to get on top of the infection early and limit its impact.
The group
Aside from technical insights, this has been a great opportunity to get inside the mind of this threat group and understand roughly how they operate and what they’re thinking. While there is currently not enough information on them to reconstruct a reliable profile, my key observations are:
- It is likely that the group is made up of more than one person, and not all members may be aware of each other;
- The group does not have specific target profiles, but most likely exploit identified vulnerabilities opportunistically, as most threat groups do;
- The group has a track record of honouring ransom payments, i.e. providing victims with decryptors once a ransom payment has been made and, in at least three confirmed cases, proved that their decryptor actually works. I do note, however, that their method of encryption is quite unreliable, meaning there’s a heightened risk that victims will not be able to decrypt their files even with RobbinHood’s assistance;
- It is likely that, if RobbinHood is operating as Ransomware as a Service (RaaS), it is designed to service a close-knit group rather than the mass-market.
Q: How did you go about conducting the investigation?
JJ: A lot of the value I provided in my investigation came out through conducting open source research. Researchers and responders are constantly uploading malware samples and discussing attacks online. Collecting that information and consolidating it allowed me to identify trends and draw conclusions about the evolution of the threat group. There was obviously a lot of technical analysis mixed in there as well. In writing up my findings, I’ve tried very hard to make sure that non-technical audiences can follow along and gain an insight into what these methods actually look like.
Q: What did you look to achieve by investigating RobbinHood?
JJ: Most of our research starts out by trying to get the information we need to advise our client, and often the deeper our research, the more value we can provide. Beyond this, as a cyber security professional, when you come across something novel or identify facts that don’t appear to be publicly known, then it’s in our best interests to contribute to the discussion and give back to the information security community. Not only will our clients be better served by the knowledge we can bring to a response, but it will mean another incident responder out there doesn’t have to start from scratch, or an affected company can access more immediate information when they need it.
Q: What should those who might be targeted by this threat group keep in mind?
JJ: The good news coming out of all of this is that RobbinHood are not doing anything unique when it comes to compromising corporate networks. This means that if you’re already confident that you have solid protections against ransomware attacks, then you’re unlikely to face any elevated risk.
However, even those with the best protections in place make mistakes, and those protections may mean nothing if they’re not periodically tested. In fact, most of the ransomware cases we respond to have stemmed from small mistakes or temporary deviations from information security best practices that have unfortunately led to devastating consequences.
The checklist of what you might want to consider is very long, but broadly my advice would be:
- Backups are a last, but vital, resort. It’s not enough to simply take backups, they need to be regularly tested, and you should try and restore one every now and again to understand how that process may work in a disaster-level incident. RobbinHood, like many other types of ransomware, tries to destroy any backups it finds, so make sure your backup systems are isolated, audited, and controlled.
- Send the activity logs from all your computers to a central database. These days this can be cheap and easy and it will be invaluable should a cyber security incident occur. This is especially important when we consider that RobbinHood actually deletes logs from each machine it infects. Because logs contain a lot of evidence into the origins and nature of an attack without them, it will take responders like myself a much longer period of time to investigate what has happened than it would otherwise.
- Lastly, and above all, make sure that your cyber security risks are represented at an executive level. If the highest levels of management don’t understand the financial liability associated with a disaster-level cyber security incident for your company, then you’re unlikely to see the appropriate level of investment and support for information security.




