Despite the allure of their media portrayal, often as an unfathomable evil lurking at the edges of society, hackers are people too.
They are subject to market forces, wants and needs, psychological tendencies, and emotions. This means that, given enough information and research, we have the tools (thanks to economists and psychologists) to model their behaviour and draw high level conclusions about the threat landscape of cybercrime.
In very broad terms (people are difficult to squeeze into boxes), we can classify cyber threat actors into the following categories. These are based upon their shared behaviours, actions, and capabilities.
- Organised cybercriminals
- Insider threats (including malicious employees and those who make honest mistakes)
- Hacktivists (such as the members of Anonymous, who act for ideological reasons)
- Unorganised threat actors (often those just starting out or lacking expertise and support)
- State-sponsored actors (who often overlap with organised criminals)
This article focuses on the capabilities of organised cybercriminals, who most likely account for the vast majority of cyber-attacks and data breaches.[1] There is still significant debate as to whether organised cybercriminals are linked to existing, more traditional criminal organisations.[2] Although it may be some time until we fully understand how these threat actors are structured, what we do know (and see every day) is that these are threat actors with organisation. This means that they may operate with the assistance of automation, playbooks, established infrastructure, and the support of a team.
The Cybercrime Ecosystem
Cyber-attacks are almost always committed by individuals, which is part of the reason why it is so difficult to understand how threat actor groups are structured. Despite this, when we dig beneath the surface of any cyber-attack or data breach, we often uncover an environment that would be difficult for one person to manage or coordinate.
This environment is supported by specialised teams, structured hierarchies, and digital marketplaces where both goods and services are sold. Maintaining this ecosystem requires investment, resources, human capital and infrastructure. As this article will demonstrate, even a seemingly simple attack, such as a phishing campaign, takes more to pull off than meets the eye.
The cybercrime environment is supported by specialised teams, structured hierarchies, and digital marketplaces where both goods and services are sold.”
Dark web marketplaces
Cybercriminals are often associated with the “dark web”, formed of websites and services not indexed by search engines. Illicit activity does take place on these sites, but arguably no more so than on the regular internet that you use every day (known as the “clear web”). Some of the most common websites that threat actors use to purchase stolen databases, for example, are hosted on the clear web.
Although there have been several notable marketplaces operating on the dark web (made more popular by the widespread adoption of cryptocurrencies), over the last few years many of these have been seized by law enforcement or abandoned by the owners in exit scams, where the owners have stolen any digital currencies entrusted to them and simply disappeared.
The impact of this has been growing distrust of the dark web (which was always inherently untrustworthy, due to participants’ anonymity). Instead, we’ve seen growing adoption of decentralised, more informal, marketplaces requiring higher levels of trust. These can commonly operate on the clear net, using everyday apps such as WhatsApp or Telegram. Their hyper-locality, the use of end-to-end encryption, and the fact that the owner does not need to worry about hosting their own infrastructure (such as websites, email, etc. all of which leave a trail) has introduced additional complications for law enforcement and security researchers alike.
Ultimately, the problem investigators face is simply "the internet" and the way it can provide protection to threat actors. The dark web, just like WhatsApp or Telegram, is a tool made for certain situations, and threat actors will often choose the tool that is most suitable for the job at hand.
A numbers game
Phishing is one of the most common and popular attack methods used by a wide variety of threat actors. It is very difficult to estimate exactly how many successful cyber-attacks begin with phishing (not least because organisations are often reluctant to report them); however, it’s likely to represent a significant percentage.
There are various authoritative studies that combine to help us build a picture of the prevalence of phishing. These studies are often conducted by those with access to primary data sets, such as Internet Servers Providers (ISPs, the companies that provide you with internet access or services), large incident response firms, and anti-malware providers.
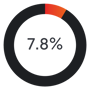
of all sent emails in 2018 were phishing emails (Symantec 2019).[3]
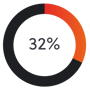
of all data breaches in 2018 involved phishing (Verizon 2019).[4]
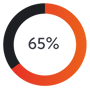
of targeted cyber attacks in 2017 involved the use of spear-phishing (Symantec 2019).[5]
Mass phishing is a large industry, and the chances that an email will successfully entice a user to click a link or download a document are low, but also reliable. This is especially true with a population that is both aging and still full of fresh targets who are relatively new to the internet. As a result, there is an entire ecosystem of threat actors dedicated to sending as many phishing emails as possible, in the hope that they can compromise at least some of the recipients.
Email lists
Data breaches happen all the time, and with each one more and more user information seeps into the public domain. It is very easy to go online and purchase lists of leaked email addresses. There are also already expansive public databases that threat actors (and cold-call marketers!) can use as potential targets.
For example, early in 2019, a database called the Collections was posted publicly online, containing over 2.2 billion email addresses. If a threat actor emailed every user on that list and only 0.1% of users engaged, that’s still over 2 million potential victims! Mass phishing is a numbers game, and given the number of people on the internet, even very small conversion rates can still be successfully monetised.
Turning clicks into profit
There is a very good reason why the business of cybercrime is expanding: it makes money. Whilst getting a user to click a link or enter their username and password doesn’t put money into anyone’s pocket, there are several diverse and innovative ways that threat actors can make money from mass phishing attacks:
- Convincing the victim to pay them. The historical scam involving a benevolent rich benefactor (traditionally the Prince of Nigeria) is still alive and going strong. However, if a threat actor has access to your emails, they can very easily create a convincing scam based on knowledge of your electricity provider or the regular invoices that your business receives.
- Committing identify fraud. If you provide information to a threat actor through a phishing scam, or they compromise your account and learn everything about you, it can be very easy for them to begin exploiting your identity. Opening a credit card in your name, for example, doesn’t require a lot of information – and more sophisticated scams could even involve impersonating you to arrange a mortgage or incorporating a business on your behalf.
- Deploying malware. There are many different types of malware, all with very different monetisation strategies; however, phishing campaigns often focus on deploying a type of malware known as bots (sometimes called Remote Access Trojans (RATs) or just Trojans). These are small pieces of code with varied capabilities. But their main benefit is that they grant the threat actor a level of control over the computers they infect. This means they can gather information, or launch more sophisticated attacks at a later date.
- Selling access. Often the quickest and safest way to make a buck is to sell access to your victim’s mailbox to someone else and make it their problem as to how they monetise it. Generally, the potential for higher revenues increases with the risk; phishing a user and selling their account online is a much less serious crime than committing identity fraud or stealing money from their account.
This might all sound rather easy, but there’s one problem: it can actually be very difficult to send high volumes of spam emails. This is because almost all ISPs use a form of blacklisting to identify and block spam email as it is happening. It can also be difficult to manage these schemes, especially if you’re dealing with millions of potential victims talking to you at once! Therefore, if a threat actor wants to persist with their operation (and yield a profit), they have to get creative; they have to become organised.
If a threat actor wants to persist with their operation (and yield a profit), they have to get creative; they have to become organised.”
Monetising Botnets
Organised threat actors that deploy bots through phishing can quickly amass millions of infected computers under their control. These networks are often sold or rented to other threat actors for a fee. Whilst the potential return on investment is lower than phishing (bear in mind that phishing-led attacks routinely see companies and high net worth individuals conned out of millions) the overall risk can be considerably lower, as the seller does not have to worry about laundering the "hot" funds acquired through phishing.
Networks of bots (called botnets) are incredibly valuable for threat actors, as they can be used in many different useful ways:
- As proxies or pivot points. This allows a threat actor to route their internet connection through hundreds or even thousands of computers before reaching their target destination. This means, for instance, if they were carrying out an online attack, it would be difficult or impossible to trace the attack back to the source or to any single device.
- To deploy additional malware. Some threat actors will buy botnets purely so they can use them to deploy their own malware, often a type of ransomware that will encrypt a user’s or company’s files and demand a ransom payment in exchange for the decryption key to restore them. This method can be instantly monetised; however, the success of the overall campaign will often depend on the quality of the computers infected by the bots in the first place.
- To leverage computing power. A large part of hacking can involve trying to crack passwords, which can take immense computing power. Some botnets can "steal" the computing power of the device they’ve infected, allowing a threat actor to utilise the computing power of devices all around the world to assist them with tasks like this.
An Organised phishing enterprise
To execute even basic phishing campaigns (for example poor-quality “Prince of Nigeria” type emails sent to millions of people) threat actors need to develop an organisation with several moving parts. This isn’t one person sitting behind a keyboard. This is an enterprise. Some of the examples of well-orchestrated phishing campaigns we’ve observed in 2019 clearly involved teams comprising the following roles.
Technical IT team
This team is only focused on making sure that the group has the necessary infrastructure in place. For example, they must prevent the organisation from being blacklisted by their ISPs, and will carry out the technical configuration involved in setting up multiple email servers.
Emailers
These are individuals whose only job is to send out emails. They’re usually not technical people at all and might not even know what they’re doing or to what end. They’re simply being paid to send emails to a list of email addresses, basically as a mass-marketer would do.
Con artists
In the event that one of these emails gets a reply, this will be escalated up the chain of experience to a dedicated team responsible for responding to potential victims. This team will be more specialised in terms of the social and communication skills required to convince a victim to hand over money.
Finance team
The finance team will be responsible for everything to do with actual transactions and the flow of funds. This could include figuring out how to open a bank account in the first place (perhaps duping an unsuspecting individual into registering a bank account and then signing over authority to the criminals). They will then determine into which bank accounts the victims are told to deposit money, and oversee the laundering operation required to extract the funds and circulate them back into their economy.
Scanning for Vulnerabilities
Another major mass-targeted activity employed by cybercriminals is systematic and automated scanning of the internet. The internet is big (and growing bigger!), new vulnerabilities are constantly being discovered, and systems are always becoming outdated (for example Windows 7, which is no longer supported by Microsoft). Because it can be difficult for even the most efficient of organisations to keep all their systems secured and up to date, threat actors are constantly scanning the entire internet looking for vulnerable machines to exploit.
Anyone who works in IT will know that as soon as you deploy a new website or service to the internet, it’s guaranteed to be scanned by something within a few minutes. It is actually relatively easy to “scan the internet”, with some researchers having demonstrated that every publicly accessible device can be scanned in under 6 minutes.
6 minutes, estimated time it takes to scan a device for vulnerabilities
Combined with a level of automation – meaning that once a vulnerability is detected it can be automatically exploited without any user interaction – threat actors can create a constant source of new devices to add to their botnets, or even try to monetise their access straight away by deploying ransomware.
Disrupt and deter
For organised cybercriminals, the threat of prosecution is simply not an effective deterrent. Rather, for those looking to counter or disrupt the cyber threat ecosystem, there are two possible approaches. First, authorities have been going after what these threat actors really want the most: money. Making it exceedingly difficult for cybercriminals to monetise their hacks – by tracing the flow of illicit funds and disrupting money laundering activities, for example – will significantly reduce their incentive to hack. As with any business, cybercriminal groups have staff to pay and infrastructure to maintain. If costs are greater than their (accessible) income, their enterprises will cease to be financially viable, or lucrative enough to warrant the effort.
Yet the advent of cryptocurrencies has made this avenue for disruption harder than it has ever been. Ransomware, for example, is actually quite a recent phenomenon in cyber security. While malware and viruses have been around for a long time, ransomware has gained momentum in tandem with the emergence of cryptocurrencies. Cryptocurrencies have allowed threat actors to monetise ransomware on a never-before-seen scale. Their victims are instructed to “legitimately” purchase a cryptocurrency with their own funds, and then transfer them to the hacker’s anonymous digital wallet. As a result, a thriving cryptocurrency-based black market has emerged through which hackers are able to liquidate their ransom money into cash.
This leaves organisations with a second option for deterring attackers: protecting themselves as much as possible
to make it harder for hackers to succeed. Insurers, cyber security specialists, legal firms and regulators are all coming together to support organisations and their in-house security teams in building resilience against an attack, by promoting best practices, providing advice, and guiding them through the implementation of effective mitigation measures.
Today, the pace of technological change and the sheer number of potential vulnerabilities available to cyber threat actors means that while organisations can make it harder for attackers to target them, they can’t make it impossible. Every device and, more commonly, every employee, supplier, distributor and contact in an organisation’s inbox, presents a potential vulnerability for a hacker to exploit. However, as discussed in this article, modern cybercriminals make calculations of risk against reward and effort against outcome, and even the most sophisticated cyber threat actor searches for the path of least resistance when planning an attack. If organisations can increase their resistance to – and resilience to – attacks sufficiently, the hacker will most likely look elsewhere. By building resilience, each organisation has the ability to reduce, as far as possible, how attractive they appear as a target in the mind of the hacker.
By building resilience, organisations can reduce how attractive they appear as a target in the mind of the hacker.”
REFERENCES
[1] Verizon Data Breach Investigations Report 2019
[2] See for example: ‘Organised crime finally embraces cyber theft’, Financial Times, 7 March 2017; ‘Cyber criminals are not who you think they are’, New Statesman, 19 October 2018
[3] Symantec Internet Security Threat Report 2019
[4] Verizon Data Breach Investigations Report 2019
[5] Symantec Internet Security Threat Report 2019




